-
Introduction:Improve website security by utilizing varied threat intelligence.
-
Category:Other
-
Added on:Jun 07 2024
-
Monthly Visitors:0.0
-
Social & Email:—
Cyberint: An Overview
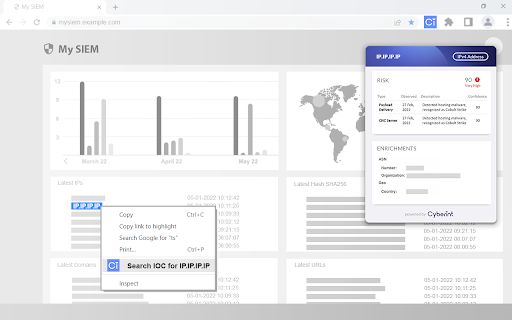
Cyberint is a powerful AI-driven Chrome extension designed to enhance the security posture of organizations by enriching Indicators of Compromise (IOCs) and Common Vulnerabilities and Exposures (CVEs) with intelligence gathered from a multitude of sources spanning the open, deep, and dark web. This tool provides a unique risk score and intelligence-based risk factors, enabling users to detect Command and Control (C2) servers, botnets, infected machines, and more, all with the click of a button. Cyberint seamlessly integrates with various web interfaces of Security Operations Center (SOC) systems, Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR) platforms, as well as blogs and news sites. It combines threat intelligence with attack surface management, giving organizations thorough visibility into their external risk exposure. By autonomously discovering all external-facing assets and leveraging intelligence from diverse web sources, Cyberint empowers cybersecurity teams to identify their most pertinent known and unknown digital risks at an earlier stage. Major global customers, including Fortune 500 companies across various industries, rely on Cyberint to prevent, detect, investigate, and remediate threats such as phishing, fraud, ransomware, brand abuse, data leaks, and external vulnerabilities, ensuring continuous protection against cyber threats.
Cyberint: Main Features
- Intelligence-based risk score
- Detection of C2 Servers, Botnets, and Infected Machines
- Autonomous discovery of external assets
- Global customer base, including Fortune 500 clients
Cyberint: User Guide
- Install the Cyberint AI Chrome extension from the Chrome Web Store.
- Open the extension and log in with your organizational credentials.
- Navigate to the desired webpage that you want to analyze.
- Click on the Cyberint extension icon to initiate the analysis.
- Review the generated risk score and intelligence-based risk factors.
- Investigate any detected C2 Servers, Botnets, or Infected Machines.
- Integrate findings with your SOC systems, SIEM, or EDR platforms for comprehensive protection.
Cyberint: User Reviews
- "Cyberint has transformed the way we handle cybersecurity threats. The ability to get real-time intelligence directly in our browser is a game-changer." - Alex T.
- "The integration with our existing security systems was seamless. We've seen a noticeable reduction in phishing incidents since using Cyberint." - Jamie L.
- "I appreciate the detailed risk scoring; it helps prioritize our response efforts effectively." - Morgan K.
FAQ from Cyberint
Latest Posts
-
 Discover 10 Groundbreaking AI Image Generators Transforming ArtistryThe integration of artificial intelligence (AI) into various technological domains has fundamentally shifted how we approach content creation. One of the most exciting applications of AI today is in image generation. These AI tools can create highly detailed and realistic images, offering countless possibilities for digital artists, marketers, and developers. Below is an extensive exploration of 10 innovative AI image generators that you need to try, complete with the latest data and user feedback.
Discover 10 Groundbreaking AI Image Generators Transforming ArtistryThe integration of artificial intelligence (AI) into various technological domains has fundamentally shifted how we approach content creation. One of the most exciting applications of AI today is in image generation. These AI tools can create highly detailed and realistic images, offering countless possibilities for digital artists, marketers, and developers. Below is an extensive exploration of 10 innovative AI image generators that you need to try, complete with the latest data and user feedback. -
 7 Game-Changing AI Tools to Transform Your Business Operations in 2024In the fast-paced world of business, staying ahead of the competition demands cutting-edge technology and innovative solutions. As we approach 2024, the integration of Artificial Intelligence (AI) tools has become an indispensable strategy for enhancing efficiency, increasing profitability, and streamlining operations. This article will introduce seven top AI business tools that can significantly boost your business operations in the upcoming year.
7 Game-Changing AI Tools to Transform Your Business Operations in 2024In the fast-paced world of business, staying ahead of the competition demands cutting-edge technology and innovative solutions. As we approach 2024, the integration of Artificial Intelligence (AI) tools has become an indispensable strategy for enhancing efficiency, increasing profitability, and streamlining operations. This article will introduce seven top AI business tools that can significantly boost your business operations in the upcoming year. -
 Discover the Top AI Image Generators of 2024Artificial Intelligence (AI) continues to revolutionize various industries, including digital art and design. The advent of AI-powered image generators has opened up a world of possibilities for artists, designers, and content creators. These tools are not just for professionals; even hobbyists can now create stunning visuals with minimal effort. As we move into 2024, several AI image generators stand out with their advanced features, user-friendly interfaces, and impressive outputs. Here are our top picks for the best AI image generators of 2024, enriched with the latest data, expert insights, and real user reviews.
Discover the Top AI Image Generators of 2024Artificial Intelligence (AI) continues to revolutionize various industries, including digital art and design. The advent of AI-powered image generators has opened up a world of possibilities for artists, designers, and content creators. These tools are not just for professionals; even hobbyists can now create stunning visuals with minimal effort. As we move into 2024, several AI image generators stand out with their advanced features, user-friendly interfaces, and impressive outputs. Here are our top picks for the best AI image generators of 2024, enriched with the latest data, expert insights, and real user reviews. -
 Top 8 AI Tools for Mastering Learning and EditingIn the fast-paced, digital-first world we live in, leveraging Artificial Intelligence (AI) tools has become crucial for enhancing learning and productivity. Whether you are a student trying to grasp complex concepts or a professional aiming to optimize your workflow, AI tools offer a myriad of features to help achieve your goals efficiently. Here, we present the best eight AI learning and editing tools for students and professionals, highlighting their unique features, user feedback, and practical applications.
Top 8 AI Tools for Mastering Learning and EditingIn the fast-paced, digital-first world we live in, leveraging Artificial Intelligence (AI) tools has become crucial for enhancing learning and productivity. Whether you are a student trying to grasp complex concepts or a professional aiming to optimize your workflow, AI tools offer a myriad of features to help achieve your goals efficiently. Here, we present the best eight AI learning and editing tools for students and professionals, highlighting their unique features, user feedback, and practical applications. -
 Best 6 AI Marketing Tools to Skyrocket Your CampaignsIn the modern digital landscape, businesses continuously seek innovative methods to enhance their marketing campaigns and achieve substantial growth. The integration of artificial intelligence (AI) in marketing has revolutionized the way companies analyze data, understand their audience, and execute their strategies. Here, we explore the six best AI marketing tools that can dramatically elevate your marketing campaigns.
Best 6 AI Marketing Tools to Skyrocket Your CampaignsIn the modern digital landscape, businesses continuously seek innovative methods to enhance their marketing campaigns and achieve substantial growth. The integration of artificial intelligence (AI) in marketing has revolutionized the way companies analyze data, understand their audience, and execute their strategies. Here, we explore the six best AI marketing tools that can dramatically elevate your marketing campaigns. -
 Top Speech-to-Text Apps for 2024As artificial intelligence (AI) continues to evolve, speech-to-text (STT) technology has seen significant advancements, streamlining various facets of both personal and professional communication. STT applications transform spoken language into written text, benefiting a wide range of users including journalists, business professionals, students, and individuals with disabilities. In this article, we will explore the top speech-to-text apps available in 2024, leveraging the latest data, features, and customer reviews to provide a comprehensive overview.
Top Speech-to-Text Apps for 2024As artificial intelligence (AI) continues to evolve, speech-to-text (STT) technology has seen significant advancements, streamlining various facets of both personal and professional communication. STT applications transform spoken language into written text, benefiting a wide range of users including journalists, business professionals, students, and individuals with disabilities. In this article, we will explore the top speech-to-text apps available in 2024, leveraging the latest data, features, and customer reviews to provide a comprehensive overview.